
At NetWorks Group, we perform full-scope penetration tests for organizations and corporations with highly mature cybersecurity programs across a variety of industries, including healthcare, finance, manufacturing, retail, and information technology. Accordingly, these organizations have robust and fine-tuned detection capabilities that challenge even the most experienced penetration testers.
Historically, there are only a finite number of ways a Red Teamer can interact with a network without setting off alarms. The following list highlights a few strategies that we have used to maintain our stealth on engagements:
• Passive information gathering (i.e. tcpdump, tshark, Wireshark)
• Slow and highly targeted enumeration of individual ports, services, and hosts (fping, nbtscan, nmap)
• Avoiding password sprays, brute-force attempts, or attempting default credentials (CME)
• Using novel or difficult-to-detect exploits (ADCS template configurations, coerced authentication, noPAC)
However, our Ethical Hacking Team has discovered another resource that allows us to be more aggressive and noisier while still maintaining a high degree of obscurity and stealth; that tool is Tailscale. Tailscale is a mesh network that uses a "zero-config" Wireguard VPN to hide its traffic and connect all of the nodes (hosts) together seamlessly as if they were all on a single LAN together.
What makes Tailscale an amazing tool for Red Teamers is its ability to turn either a compromised host -- or the Red Team's drop box -- into a subnet router, exposing the entire target network to the Red Team remotely. Let's look at the below diagram to see how amazing this is to a Red Team:
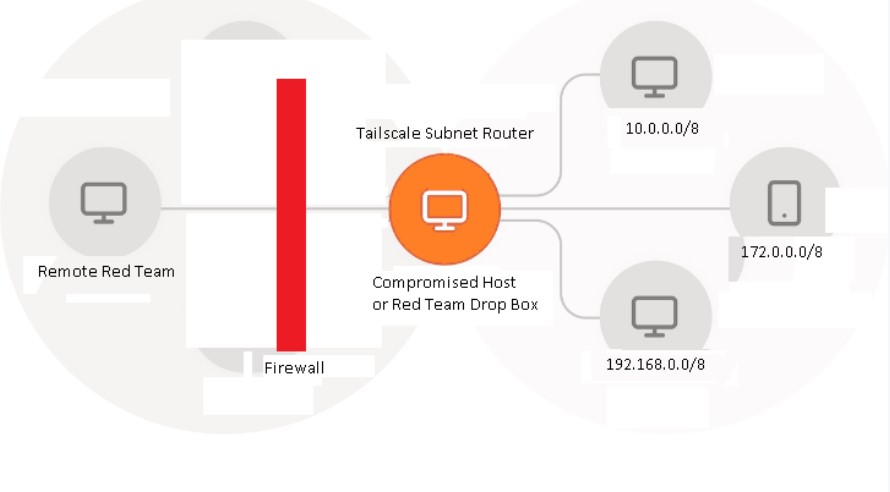
As you can see, the Red Team has full, remote access to all of the 10.0.0.0/8, 172.0.0.0/8, and 192.0.0.0/8 networks in this organization. Take a step back and think that through -- when the Red Teamer, at their home location, using their own machine, launches an attack, the traffic is passed through the compromised host and onto the final target; the traffic is not coming from the host internally. Not only does this make it very difficult to determine the origin of the activity/attack, but the traffic itself is obfuscated leaving only the targeted host or user account as evidence that something has occurred. Effectively, Tailscale can serve as a pseudo command-and-control framework using a legitimate executable or binary, something that will not be identified as malware on the network.
In our experience, organizations that have historically caught Red Team activities have failed to do so when they’re performed (i.e. obfuscated) via Tailscale. Organizations that were able to detect something were unable to pinpoint who, what, or from where the activity originated. Needless to say, Tailscale has become an essential tool in our Ethical Hacking Team toolbox.
If you're a Red Teamer or cybersecurity researcher with similar experiences with Tailscale -- or would like to collaborate further on this topic -- please reach out via LinkedIn or Twitter; we'd love to hear from you!
###
Authored By: Chris Neuwirth, Senior Penetration Tester, NetWorks Group
Publish Date: September 22, 2022







